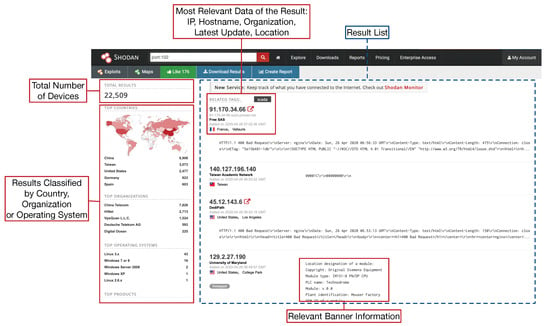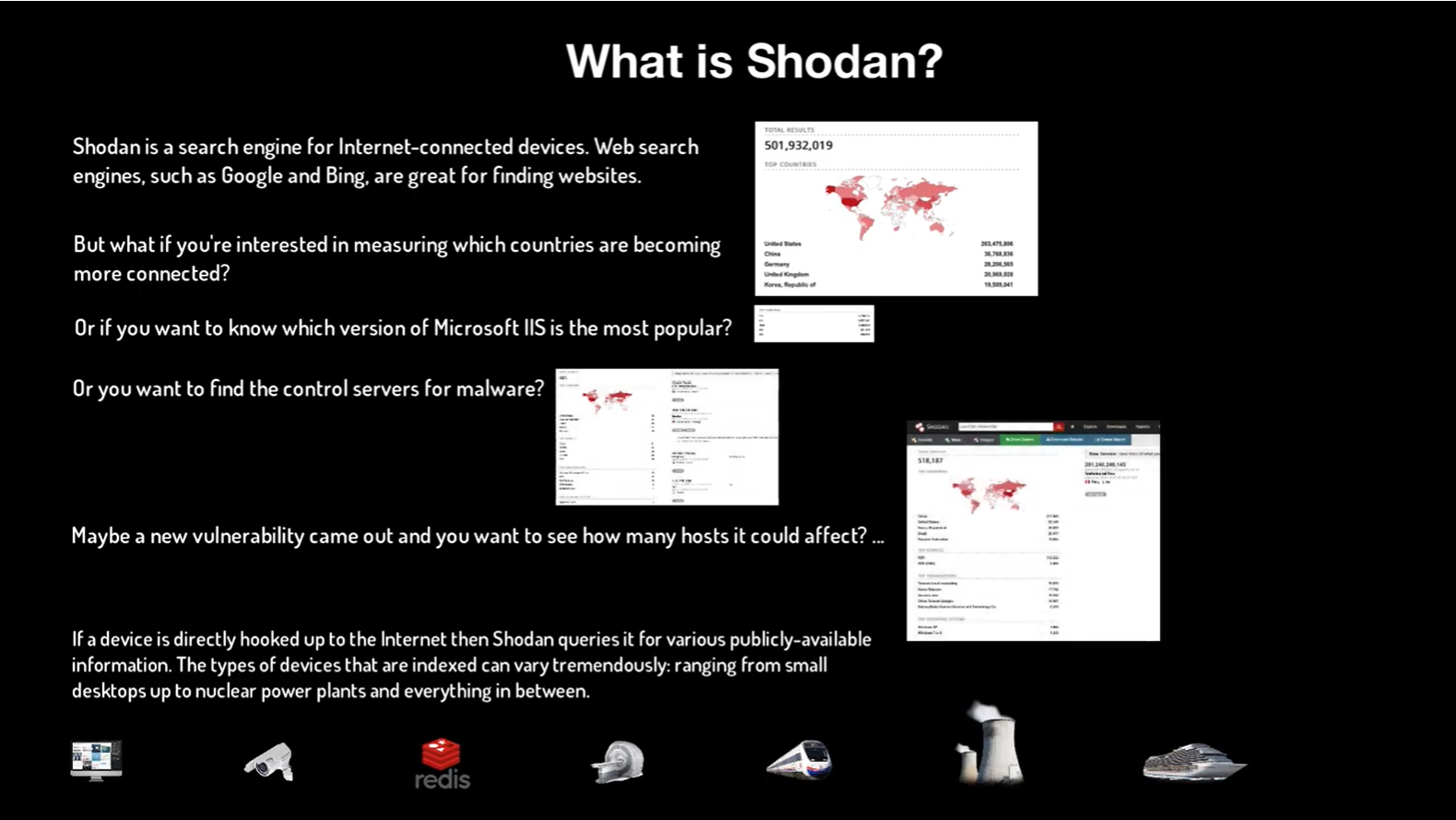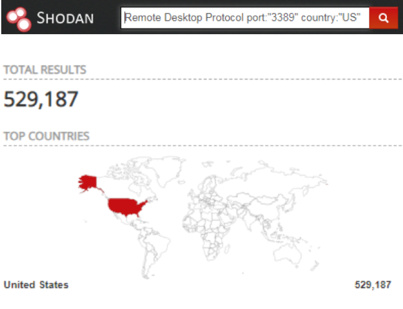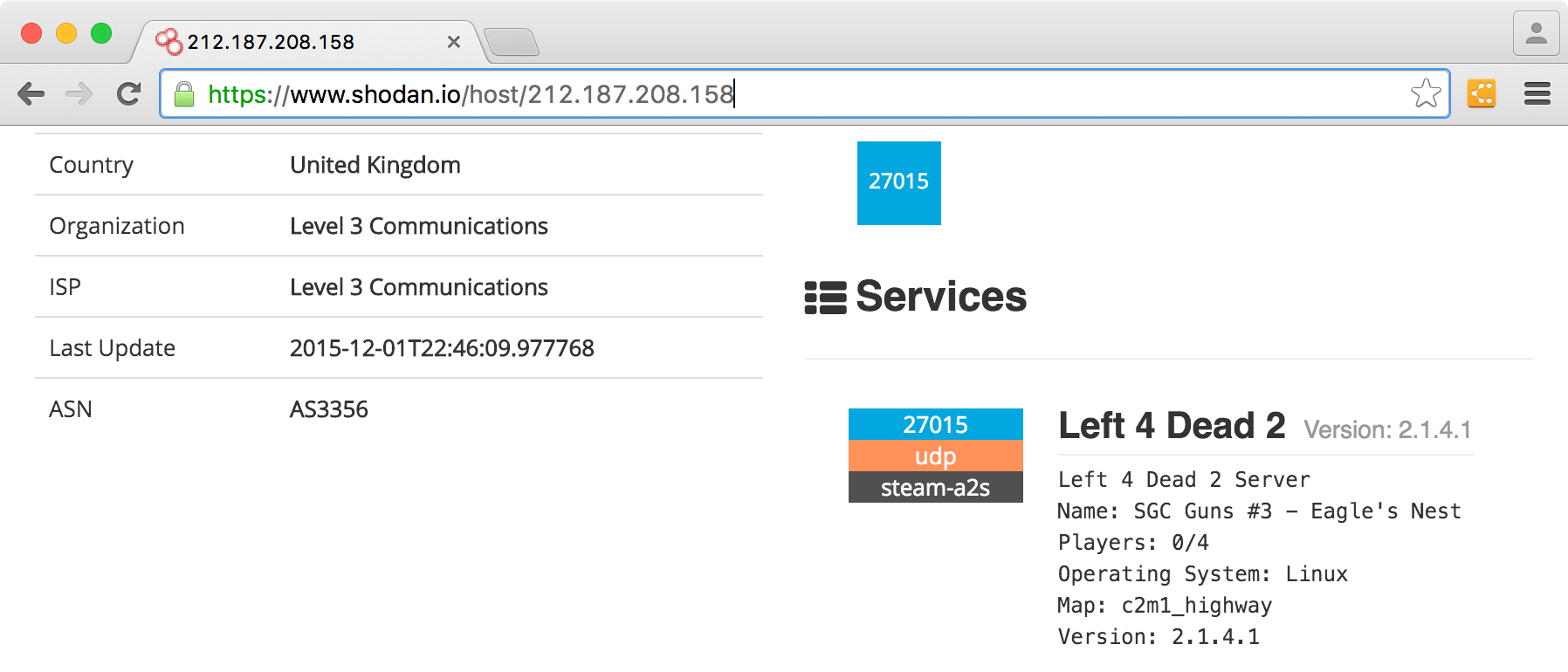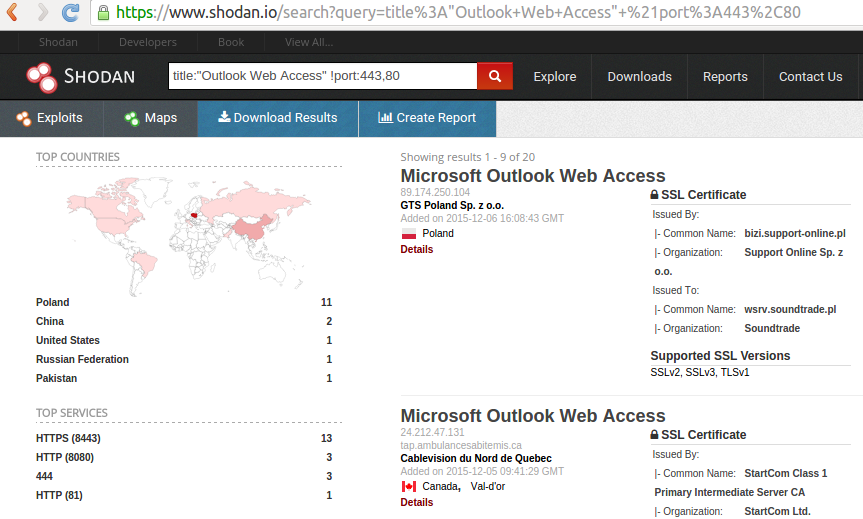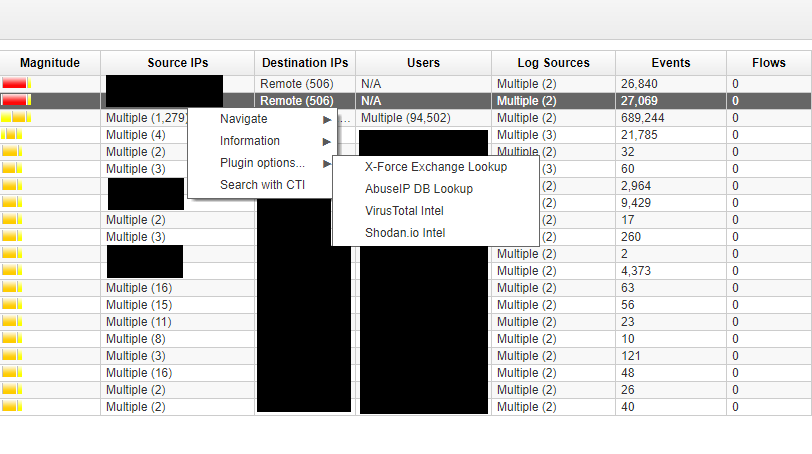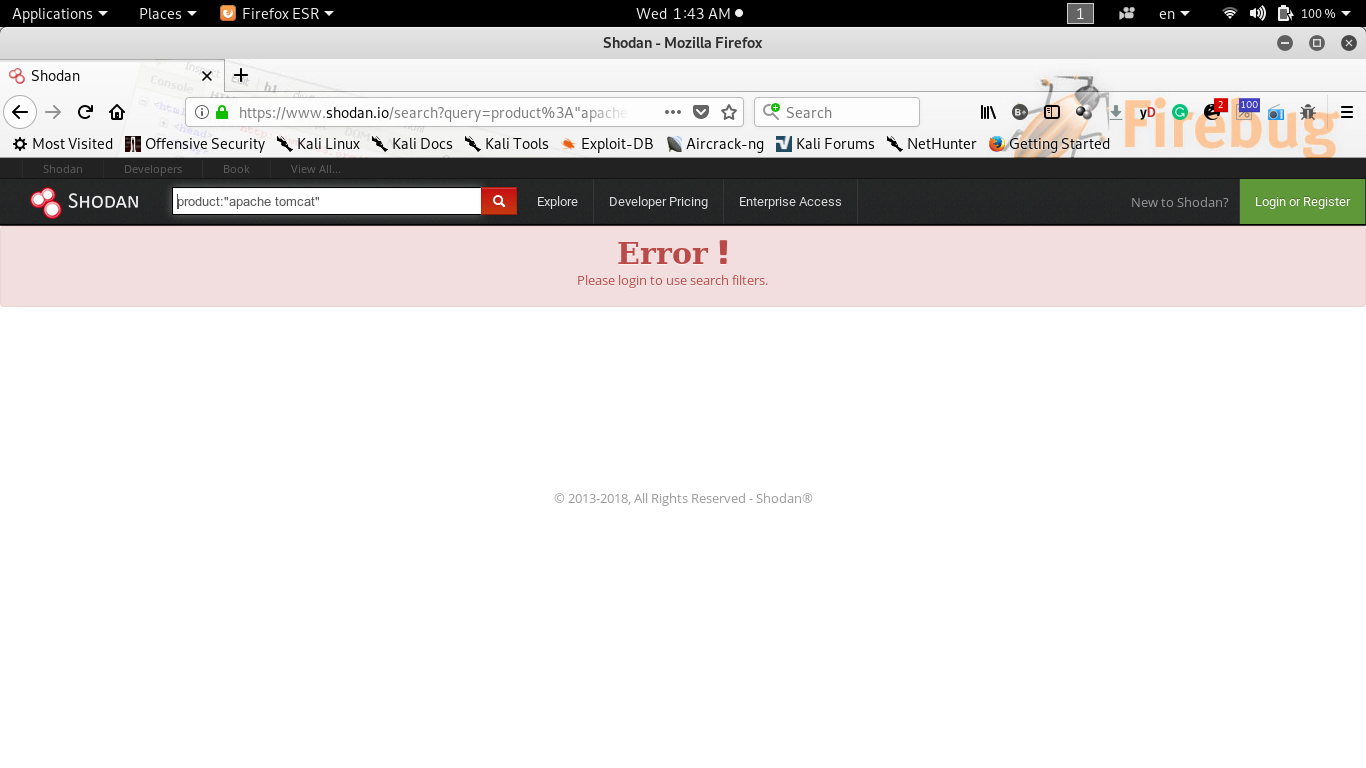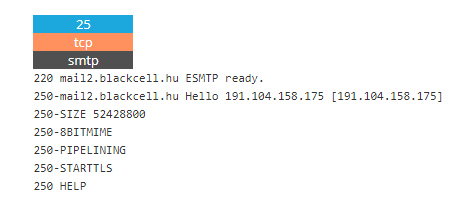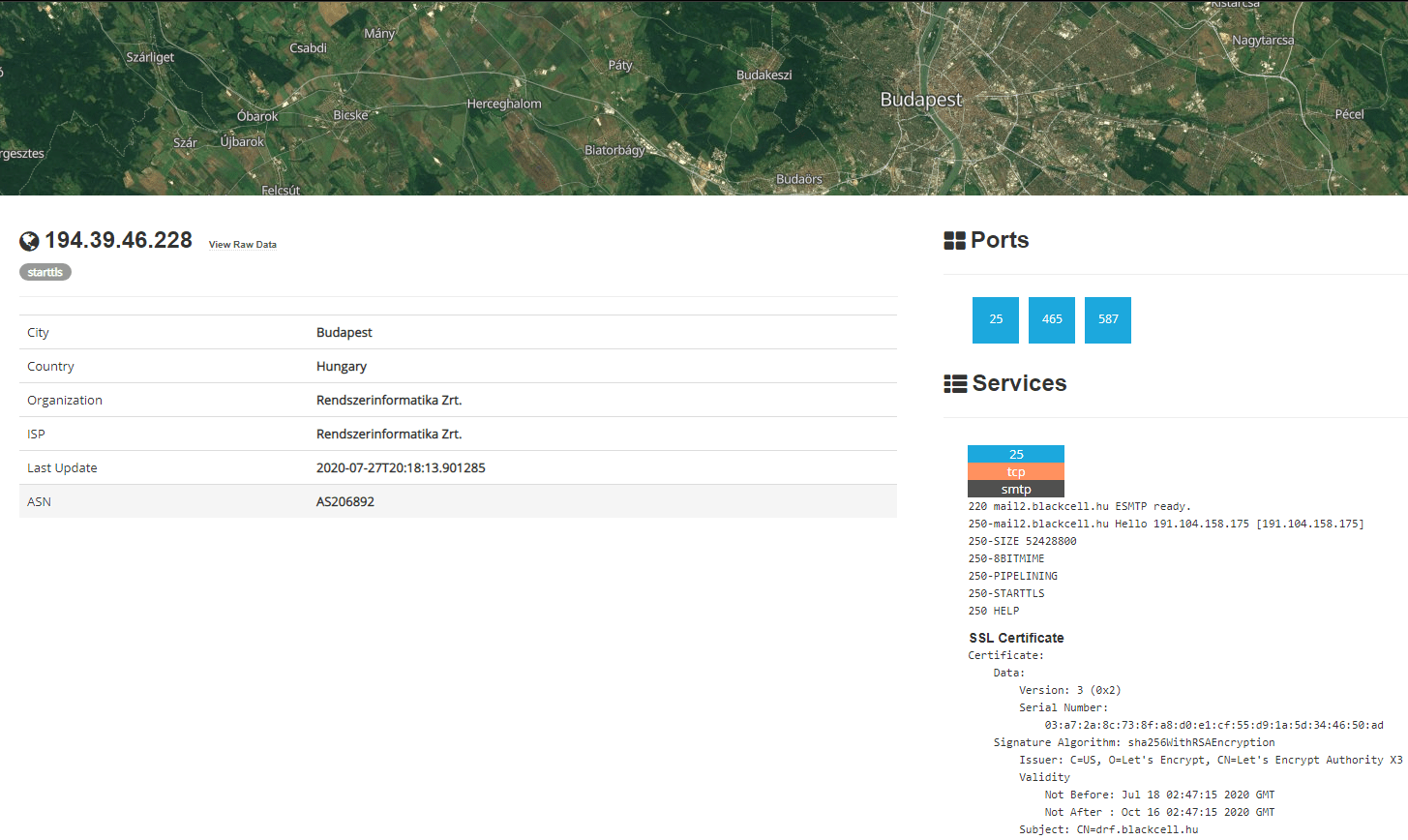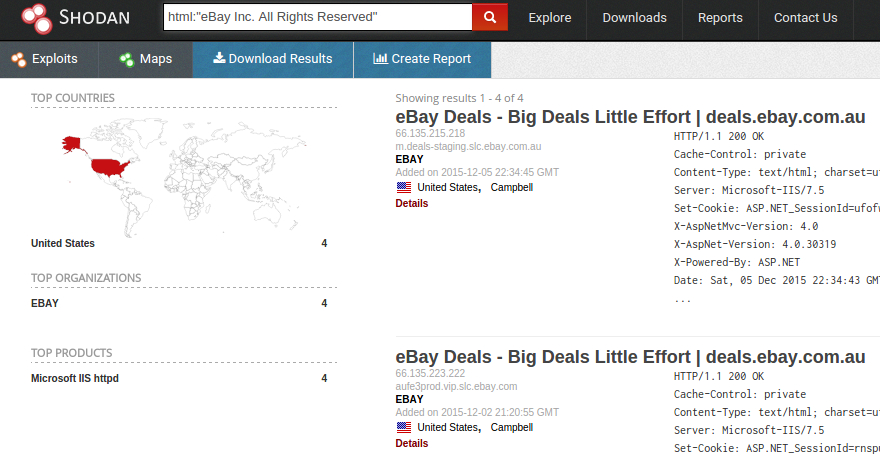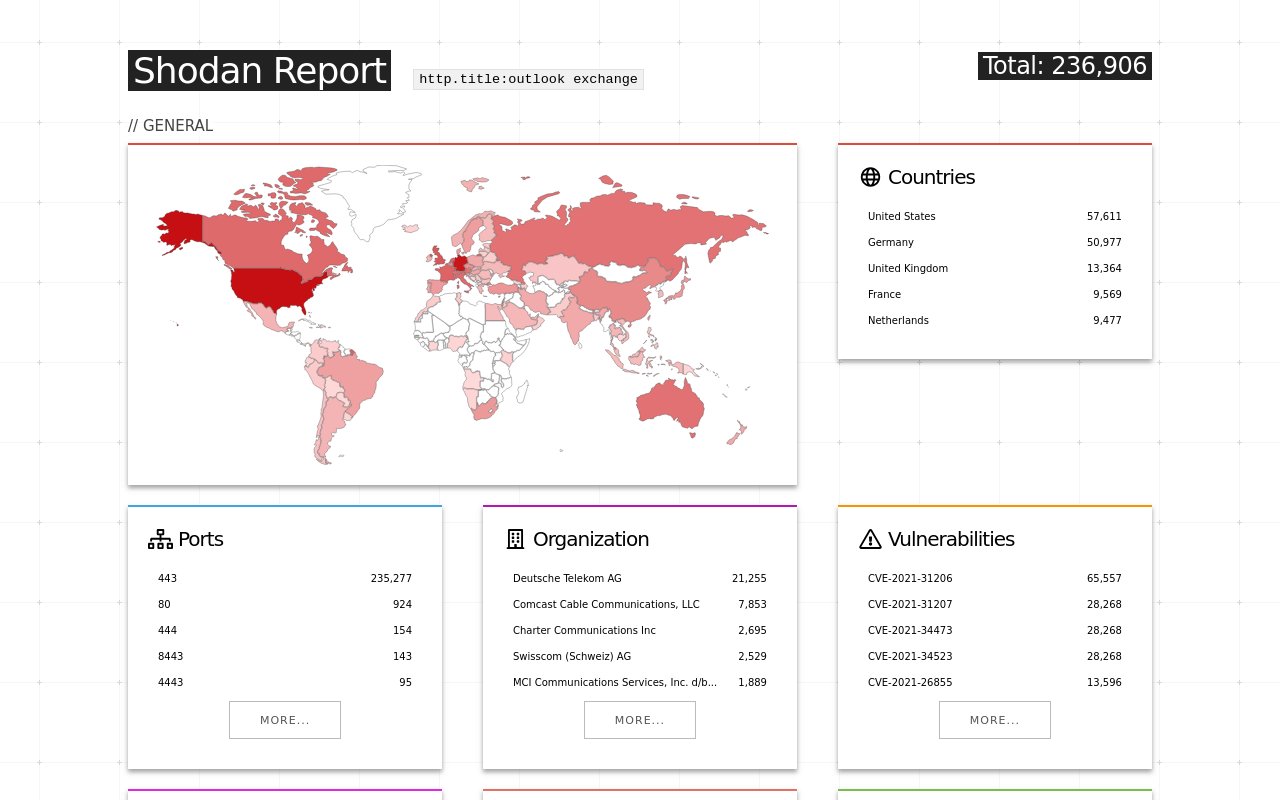
Shodan on Twitter: "More than 18% of Exchange servers remain unpatched for the ProxyShell vulnerability. Nearly 40% are vulnerable to CVE-2021-31206: https://t.co/7yetz9GoJw https://t.co/0r2AOQsibB" / Twitter

Shodan on Twitter: "Not sure what search filters are available? Check out our new filter reference page: https://t.co/kDlGDgpFms https://t.co/bUJX1D8ChQ" / Twitter

Shodan founder John Matherly on IoT security, dual-purpose hacking tools, and information overload | The Daily Swig
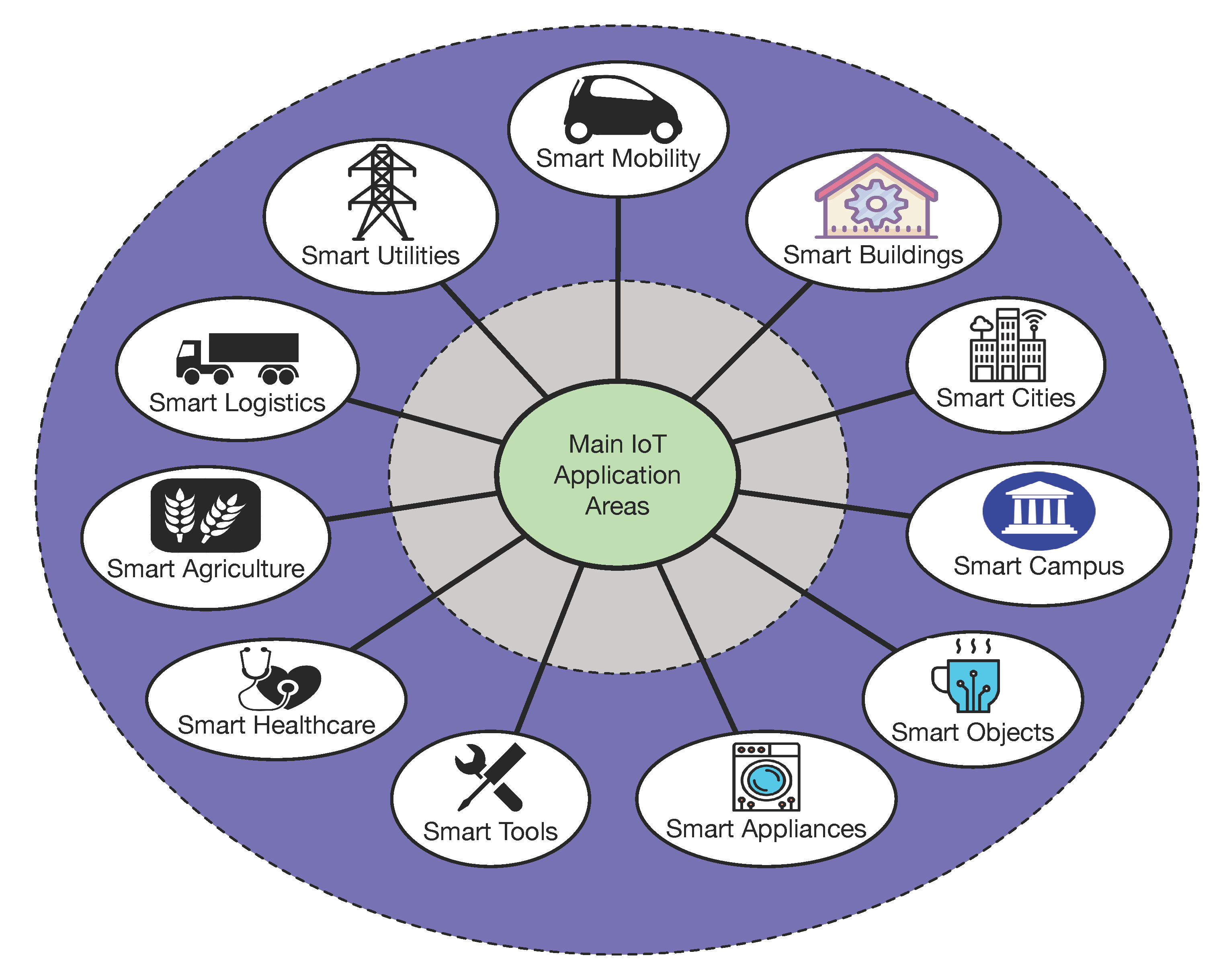
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases